This super-fast 3-port Anker wall charger is a bargain now at 35% off
One of the more annoying things about buying modern tech is that some manufacturers aren’t including charger plugs (also known as power adapters) in the box. But there’s a silver lining here! It gives you the chance to grab something that’s way better than they would’ve given you—like this super-fast 3-port Anker Nano wall plug for $36 (was $55).
That’s a fantastic price, and it even comes with a free USB-C-to-C cable that lets you take full advantage of its power. With two USB-C ports and a USB-A port, you can reliably charge any of your devices, and those USB-C ports offer up to 100W of charging, which is especially great for laptops. With all three ports charging simultaneously, the power is split down to 45W, 30W, and 18W max per port, respectively.
This charger is built on newer GaN tech, something we love to see because GaN chargers are faster, smaller, and safer, with better temperature regulation, less heat output, and protections against short circuits. This power brick is portable, too, with its small size and prongs that fold in to prevent damage and scratching. The included cable is 5 feet long, so you can comfortably charge while in bed.
It’s only $36 right now and that’s an incredible price for a fast-charging wall plug as versatile as this one, so don’t miss out on this limited-time deal. Grab this USB charger block while you can!
Save 35% on this fast 3-port USB wall charger, plus free cableBuy now at Amazon 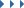
© 2025 PC World 1:45am  
|
Was your data stolen in the AT&T breaches? You may be entitled to money
Back in 2019, hackers stole account data for roughly 74 million AT&T landline customers—including social security numbers. AT&T didn’t disclose the discovery until early 2024, when the data leaked on the dark web. Then several months later, AT&T revealed attackers also stole call data records for over 100 million wireless customers between May 1 and October 31, 2022, including those subscribed to its subsidiaries Cricket Wireless and H2O Wireless.
In response, a bunch of people got together, sued AT&T, and won.
More importantly, a judge recently granted preliminary approval to settlement terms. As it currently stands, $177 million will be distributed to those caught up in these data breaches. This includes both current and former AT&T customers. For the 2019 breach, $148 million is set aside, while the 2024 breach gets a pool of $28 million.
Payments will vary depending on how severely you were affected, with those who have documents proving damages directly related to the AT&T data leaks entitled to larger amounts. Landline customers part of the 2019 breach can get up to $5,000. Wireless customers impacted by the 2024 breach are entitled to up to $2,500.
As stated in the approval filing, eligible customers will receive a notice by physical mail or email beginning on August 4, 2025. The notice period is expected to finish by October 17, 2025. All claims must be made by November 18, 2025.
The settlement’s final approval is scheduled for December 3, 2025, which must first happen before payments begin.
Besides waiting for the notice, you should also take further steps to mitigate the effect of these major data leaks—strengthening your passwords (especially for those compromised or used on more than one site), locking down your financial life, watching out for potential scams, and keeping up with the news. Our full guide will walk you through each of these steps. They’re sadly necessary in this age of endless data leaks and breaches. 
© 2025 PC World 1:25am  
|
|
|
 |
 
|
The big lesson from the huge security flaw in Brother printers
Last week, worrying news surfaced for millions of printer owners: Over 689 models of Brother printers are open to attack, along with 53 additional models made by Fujifilm, Konica, Minolta, Ricoh, and Toshiba. (As if dealing with home printers wasn’t already enough of a headache already.) Worse, eight different flaws are exploitable, with one unpatchable.
The problem: The default administrator password on Brother printers (and those using Brother components) can be guessed, in part by exploiting other vulnerabilities in these devices. But a firmware update won’t be able to address this issue, as what your printer ships with is already set.
Fortunately, you can fix this problem yourself by changing the default administrator password. Also make sure you update your printer to patch the other seven bugs—through them, a bad actor could steal stored scans, look at your saved contacts, change your settings, and even execute commands.
Our favorite password manager
Dashlane
Read our review
Best Prices Today:
$4.99 at Dashlane
The lesson here? Always change the password when setting up a new device. Think not just printers, but also routers, baby monitors, and anything else that ships with a default username and password. Manufacturers now give devices unique passwords (unlike the dark ages where all models would use password or nothing at all), but as this Brother incident illustrates, the practice doesn’t guarantee truly random, secure login info.
This task is easy with a password manager—it handles the work of generating and remembering random, strong passwords for you. Because a secondary lesson is that if you create passwords by taking part of a phrase or word related to the app or website, adding something extra to it, and then calling it a day, whatever you’ve come up with is likely too weak. Brother’s method was similar (though with some extra steps), and… well, here we are. 
© 2025 PC World 1:25am  
|
|
|